Guide you step by step to How to install and run Backtrack on android. As the Backtrack is also available with ARM architecture which makes it possible to run Backtrack on an ARM machine such as mobiles or tablets.
Recently, We are discussed Install and Run BackTrack on Windows. Android is the best OS for penetration testing. It designed for digital forensics and penetration testing or hacking tool. It comes with many more updated tools. As the Backtrack is also available with ARM architecture which makes it possible to run Backtrack on an ARM machine such as mobiles or tablets.
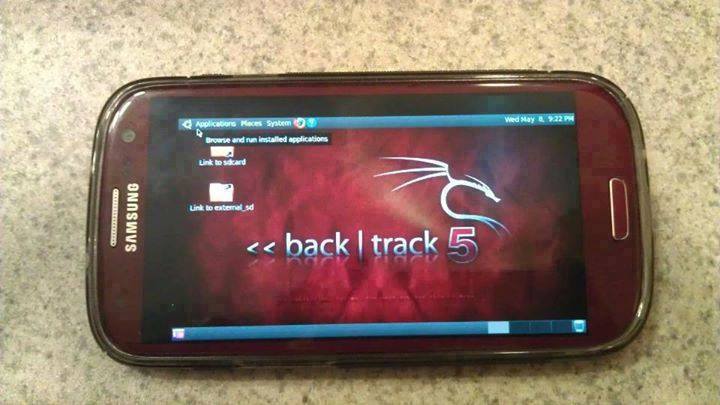
How To Install and Run Backtrack On AndroidRequirements
- A Rooted Device [ Root Simple Android Phone Without Pc ]
- Backtrack ARM [ Download ]
- BusyBox [ Download ]
- Android Terminal and Android VNC
- If you are using PC then you need 7zip for extraction otherwise you can use zarchiver on your android phone. [ Download ]
Step to Install and Run Backtrack On Android:
First of all extract the BT5-GNOME-ARM.7z. and copy the "BT5" folder and then put in your phone's root directory. Here mine phone is /sdcard. The root directory is different for different mobile devices.
- Now install all the above apps Busybox, Android Terminal, Android Vnc.
- After installing BusyBox application open it and wait until it finishes loading and then click on Smart install.
- Now open the android terminal and type the following command:
su cd /sdcard/BT5sh bootbtNOTE :- When you type su in terminal it will ask you for superuser request and you have to tap on Grant. - After this, type the following commands in terminal.
export USER=rootvncpasswd - After entering vncpasswd the terminal will ask you to enter the password. Enter the desired password and hit enter.
- Now type the following commands.
tightvncserver -geometry 1280×720 - The terminal emulator will create the localhost to connect it to VNC server. Now note the localhost port marked red below. Now minimize the terminal emulator.
- Open the Android VNC and type the following settings.
Nickname : BT5
Password : your password here which you entered in terminal (step no.6)
Address : localhost
Port : 5906
Password : your password here which you entered in terminal (step no.6)
Address : localhost
Port : 5906
NOTE: Make sure that your localhost's port matches with terminal's localhost. Here mine New 'X' desktop is localhost:6. You may be different. So, in VNC type Port 590X where the "X" is the localhost in the android terminal.
That's it now just tap on connect to run the Backtrack on your android. So in this way you successfully install and run backtrack 5 on android. If you face any problem feel free to discuss in below comments!
- Hacking Tools For Mac
- Pentest Tools Online
- Pentest Tools Review
- What Are Hacking Tools
- Tools For Hacker
- Hacking Tools For Windows 7
- Pentest Tools Online
- Tools 4 Hack
- Hacker Tool Kit
- Pentest Reporting Tools
- Hack Tools
- Hacking Tools Windows 10
- Pentest Tools For Android
- Hacking Apps
- World No 1 Hacker Software
- Hack Tools
- Pentest Tools Bluekeep
- Growth Hacker Tools
- Growth Hacker Tools
- Tools Used For Hacking
- Hackers Toolbox
- Hack Apps
- Hack Tool Apk
- Hack Tools Online
- Hacking Apps
- Blackhat Hacker Tools
- Pentest Tools Subdomain
- Hacker Tools Github
- Hacking Tools Online
- Pentest Tools Website
- What Are Hacking Tools
- Easy Hack Tools
- Hacker Tools Github
- Hacking Tools And Software
- Hack And Tools
- Tools For Hacker
- Pentest Tools Tcp Port Scanner
- Hacking Tools For Pc
- Termux Hacking Tools 2019
- Pentest Recon Tools
- Hacker Hardware Tools
- Pentest Tools Tcp Port Scanner
- Hacking Tools Usb
- Pentest Tools Free
- Hacker Tools Apk Download
- Tools Used For Hacking
- Hacker Tools Software
- Growth Hacker Tools
- Hack Tools For Windows
- Best Hacking Tools 2020
- Hacker Tools Online
- Hacker Tools For Pc
- Hack Rom Tools
- Pentest Tools List
- Nsa Hack Tools
- Free Pentest Tools For Windows
- Hacker Tools For Windows
- Hacking Tools Online
- Pentest Tools Nmap
- Pentest Tools Alternative
- Hack Tools For Pc
- Hack Tool Apk No Root

No comments:
Post a Comment